Share real and effective CompTIA Network+ N10-006 exam dumps for free. 40 Online N10-006 Exam Practice test questions and answers, online N10-006 pdf download and YouTube video learning, easy to learn! Get the full N10-006 Dumps:https://www.leads4pass.com/n10-006.html (1703 Q&A) to make it easy to pass the exam!
CompTIA Network+ covers the configuration, management, and troubleshooting of common wired and wireless network devices. Also included are emerging technologies such as unified communications, mobile, cloud, and virtualization technologies.
[PDF] Free CompTIA Network+ N10-006 pdf dumps download from Google Drive: https://drive.google.com/open?id=1oME3_Ww4GaPrmj9dRokJJL9iC6d4agEQ
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
Network+ Certification | CompTIA IT Certifications: https://certification.comptia.org/certifications/network
Latest effective CompTIA Network+ N10-006 Exam Practice Tests
QUESTION 1
A technician is reviewing the following aggregated information on a server to determine the cause of a user\\’s
connection problem: Which of the following is the technician reviewing?
Which of the following is the technician reviewing?
A. Syslog server logs
B. Application logs
C. Network sniffer logs
D. SNMPv2 queries
Correct Answer: A
Syslog server logs are the logs that are saved on a system whenever an instance happens of the wireless device.
Reviewing the logs can help him understand the behavior of the WAP as well as the client.
QUESTION 2
A network technician is tasked with designing a firewall to improve security for an existing FTP server that is on the
company network and is accessible from the internet. The security concern is that the FTP server is compromised it
may be used as a platform to attack other company servers. Which of the following is the BEST way to mitigate this
risk?
A. Add an outbound ACL to the firewall
B. Change the FTP server to a more secure SFTP
C. Use the implicit deny of the firewall
D. Move the server to the DMZ of the firewall
Correct Answer: D
QUESTION 3
Users are reporting extreme slowness across the network every Friday. Which of the following should the network
technician review first to narrow down the root cause of the problem?
A. Baseline
B. Bottleneck
C. Utilization
D. Link status
Correct Answer: C
QUESTION 4
A technician wants to configure the inbound port of a router to prevent FTP traffic from leaving the LAN. Which of the
following should be placed on the router interface to accomplish this goal?
A. Static routes for all port 80 traffic
B. DHCP reservations for all /24 subnets
C. ACL for ports 20 and 21
D. MAC filtering using wildcards
Correct Answer: C
QUESTION 5
An administrator\\’s router with multiple interfaces uses OSPF. When looking at the router\\’s status, it is discovered that
one interface is not passing traffic. Given the information below, which of the following would resolve this issue? Output:
Fast Ethernet 0 is up, line protocol is down Int ip address is 10.20.130.5/25 MTU 1500 bytes, BW10000 kbit, DLY 100
usec Reliability 255/255, Tx load 1/255, Rx load 1/255 Encapsulation ospf, loopback not set Keep alive 10 Full duplex,
100Mb/s, 100 Base Tx/Fx Received 1052993 broadcasts 0 input errors 0 packets output, 0 bytes 0 output errors, 0
collisions, 0 resets
A. Set the loopback address
B. Enable the connecting port
C. Put the IP address in the right broadcast domain
D. Replace the line card
E. Set OSPF to area 0
Correct Answer: B
QUESTION 6
A company recently added an addition to their office building. A technician runs new plenum network cables from the
switch on one side of the company\\’s gymnasium 80 meters (262 ft.) to the new offices on the other side, draping the
wires across the light fixtures. Users working out of the new offices in the addition complain of intermittent network
connectivity. Which of the following is MOST likely the cause of the connectivity issue?
A. dB loss
B. Distance
C. Incorrect connector type
D. EMI
E. Crosstalk
Correct Answer: D
QUESTION 7
A network architect is designing a highly redundant network with a distance vector routing protocol in order to prevent
routing loops, the architect has configured the routers to advertise failed routes with the addition of an infinite metric.
Which of the following methods has the architect chosen?
A. Spanning tree
B. Split horizon
C. Route poisoning
D. Hold down timers
Correct Answer: C
https://books.google.co.za/books?id=C5G6DAAAQBAJandpg=PT1507andlpg=PT1507anddq=adv
ertise+failed+routes+with+the+addition+of+an+infinite+metricandsource=blandots=hPhUeuDuis
andsig=d2zmlLrjHOSadqWLfeFEPjfNJjUandhl=enandsa=Xandved=0ahUKEwi_z9Gr5vXQAhUhJM
AKHRFHCeQQ6AEIGjAA#v=onepageandq=advertise%20failed%20routes%20with%20the%
20addition%20of%20an%20infinite%20metricandf=false
QUESTION 8
An IP address is encapsulated at which of the following layers of the OSI model?
A. Transport
B. Data link
C. Network
D. Application
Correct Answer: C
QUESTION 9
A technician is installing a switch that will be used for VoIP and data traffic. The phones do not support the 802.3af
standard. Which of the following should the technician configure on the switch?
A. VLAN
B. PoE
C. VTP
D. QoS
Correct Answer: D
QUESTION 10
A network technician has configured a new firewall with a rule to deny UDP traffic. Users have reported that they are
unable to access Internet websites. The technician verifies this using the IP address of a popular website. Which of the
following is the MOST likely cause of the error?
A. Implicit deny
B. HTTP transports over UDP
C. Website is down
D. DNS server failure
Correct Answer: A
In a network firewall ruleset if a certain type of traffic isn\\’t identified it will be denied or stopped by Implicit Deny.
QUESTION 11
Which of the following ports should be allowed through a firewall to allow DNS resolution to occur to an outside DNS
server?
A. 20
B. 53
C. 80
D. 3389
Correct Answer: B
QUESTION 12
Two switches are connected using both a CAT6 cable and a CAT5e cable. Which of the following problems is
occurring?
A. Missing route
B. Autosensing ports
C. Improper cable types
D. Switching loop
E. Media mismatch
Correct Answer: D
QUESTION 13
Which of the following network protocols is used to resolve FQDNs to IP addresses?
A. DNS
B. FTP
C. DHCP
D. APIPA
Correct Answer: A
An Internet service that translates domain names into IP addresses. Because domain names are alphabetic, they\\’re
easier to remember. The Internet however, is really based on IP addresses. Every time you use a domain name,
therefore, a DNS service must translate the name into the corresponding IP address. For example, the domain name
www.example.com might translate to 198.105.232.4.
QUESTION 14
PKI is a method of user authentication which uses which of the following?
A. Various router commands
B. Access control lists
C. Certificate services
D. A RADIUS server
Correct Answer: C
Explanation: A PKI (public key infrastructure) enables users of a basically unsecure public network such as the Internet
to securely and privately exchange data and money through the use of a public and a private cryptographic key pair that
is obtained and shared through a trusted authority. The public key infrastructure provides for a digital certificate that can
identify an individual or an organization and directory services that can store and, when necessary, revoke the
certificates. Although the components of a PKI are generally
QUESTION 15
During a check of the security control measures of the company network assets, a network administrator is explaining
the difference between the security controls at the company. Which of the following would be identified as physical
security controls? (Select THREE).
A. RSA
B. Passwords
C. Man traps
D. Biometrics
E. Cipher locks
F. VLANs
G. 3DES
Correct Answer: CDE
Physical security is the protection of personnel, hardware, programs, networks, and data from physical circumstances
and events that could cause serious losses or damage to an enterprise, agency, or institution. This includes protection
from fire, natural disasters, burglary, theft, vandalism, and terrorism.
C: A mantrap is a mechanical physical security devices for catching poachers and trespassers. They have taken many
forms, the most usual being like a large foothold trap, the steel springs being armed with teeth which met in the victim\\’s
leg.
D: Biometric authentication is a type of system that relies on the unique biological characteristics of individuals to verify
identity for secure accessto electronic systems. Biometric authentication is a physical security device.
E: Cipher locks are used to control access to areas such as airport control towers, computer rooms, corporate offices,
embassies, areas within financial institutions, research and development laboratories, and storage areas holding
weapons, controlled substances, etc. Cipher locks are physical security devices.
QUESTION 16
Which of the following describes an IPv6 address of ::1?
A. Broadcast
B. Loopback
C. Classless
D. Multicast
Correct Answer: B
The loopback address is a special IP address thatis designated for the software loopback interface of a computer. The
loopback interface has no hardware associated with it, and it is not physically connected to a network. The loopback
address causes any messages sent to it to be returned to the sendingsystem. The loopback address allows client
software to
Pass Your Certification With Marks4sure Guarantee 41 CompTIA N10-006 : Practice Test
communicate with server software on the same computer. Users specify the loopback address which will point back to
the computer\\’s TCP/IP network configuration.
In IPv4, the loopback address is 127.0.0.1.
In IPv6, the loopback address is 0:0:0:0:0:0:0:1, which can be shortened to ::1
QUESTION 17
Which of the following DNS records allows for reverse lookup of a domain?
A. PTR
B. AAAA
C. A
D. MX
Correct Answer: A
QUESTION 18
A client\\’s computer is unable to access any network resources. Which of the following utilities can a technician use to
determine the IP address of the client\\’s machine?
A. ipconfig
B. nslookup
C. dig
D. tracert
Correct Answer: A
Explanation: ipconfig is a commmand line utility available on all versions of Microsoft Windows starting with Windows
NT. ipconfig is designed to be run from the Windows command prompt. This utility allows you to get the IP address
information of a Windows computer. It also allows some control over active TCP/IP connections. ipconfig is an
alternative to the older \\’winipcfg\\’ utility.
QUESTION 19
An administrator would like to search for network vulnerabilities on servers, routers, and embedded appliances. Which
of the following tools would MOST likely accomplish this?
A. Baseline analyzer
B. Ping
C. Protocol analyzer
D. Nessus
Correct Answer: D
QUESTION 20
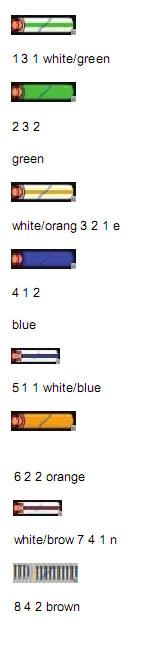
A technician tests a cable going to the patch panel and notices the following output from the cable tester:
1——————1 2——————2 3——————3 4——————4 5——————5 6——————6 7——————7
8——————8
On a T568A standard CAT5e cable, which of the following wire strands is the cause of this connectivity issue?
A. White Orange
B. Solid Brown
C. Solid Orange
D. White Green
Correct Answer: D
T568A Wiring
Pi Pai Wir Color n r e
QUESTION 21
Which of the following records allows for reverse DNS lookups?
A. AAAA
B. A
C. PTR
D. CNAME
Correct Answer: C
QUESTION 22
Which of the following network elements enables unified communication devices to connect to and traverse traffic onto
the PSTN?
A. Access switch
B. UC gateway
C. UC server
D. Edge router
Correct Answer: B
People use many methods of communication nowadays such as voice, email, video and instant messaging. People also
use many different devices to communicate such as smart phones, PDAs, computers etc.Unified Communications (UC)
enables people using different modes of communication, different media, and different devices to communicate with
anyone, anywhere, at any time.
Many communication methods use digital signals. To send a digital signal over the analog PSTN, you need a gateway
(in this case a UC Gateway) to convert the digital signals into an analog format that can be sent over the PSTN.
QUESTION 23
A network administrator needs to ensure there is no same channel interference for an 802.11n deployment with four
WAPs. Which of the following channel setting configurations meets this criteria when using 40 MHz channels?
A. 36, 40, 44, 48
B. 36, 44, 52, 60
C. 36, 44, 48, 52
D. 36, 48, 60, 64
Correct Answer: B
QUESTION 24
A technician is configuring a new DSL router. The technician can communicate with the LAN, but not the WAN. Which of
the following is the MOST likely cause?
A. Duplicate IP addresses
B. Bad GBIC
C. Wrong gateway
D. Switching loop
Correct Answer: C
QUESTION 25
Which of the following cables would BEST be used to extend a network through an 80 feet (262 meters) machine shop
that has many high voltage machines and generators running?
A. CAT5
B. CAT6
C. Coaxial
D. Fiber
Correct Answer: D
QUESTION 26
Which of the following security devices can receive and process HTTP requests from hosts to allow or deny traffic for
web browsing purposes only?
A. Load balancer
B. VPN concentrator
C. Proxy server
D. DNS server
Correct Answer: C
QUESTION 27
The ISP needs to terminate the WAN connection. The connection should be located in the network server room where
the company LAN equipment resides. Which of the following identifies the location?
A. Smart jack
B. MDF
C. VPN
D. 66 block
Correct Answer: B
Short for main distribution frame, a cable rack that interconnects and manages the telecommunications wiring between
itself and any number of IDFs. Unlike an IDF, which connects internal lines to the MDF, the MDF connects private or
public lines coming into a building with the internal network.
QUESTION 28
Ann, a network administrator, is in the process of cleaning network switches for resale. Ann splashes the cleaning agent
in her eye and needs to know the procedure of cleansing her eye. To which of the following should Ann refer?
A. EULA
B. MSDS
C. SLA
D. MOU
Correct Answer: B
QUESTION 29
Which of the following describes a design where traffic is shared between multiple network servers to provide greater
throughput and reliability?
A. Load balancing
B. MPLS trunking
C. VLAN tagging
D. Multiplexing
Correct Answer: A
QUESTION 30
A company has a server with redundant power supplies. Which of the following is this an example of?
A. Traffic shaping
B. Caching engines
C. Fault tolerance
D. Load balancing
Correct Answer: C
QUESTION 31
A network technician has set up an FTP server for the company to distribute software updates for their products. Each
vendor is provided with a unique username and password for security. Several vendors have discovered a virus in one
of the security updates. The company tested all files before uploading them but retested the file and found the virus.
Which of the following could the technician do for vendors to validate the proper security patch?
A. Use TFTP for tested and secure downloads
B. Require biometric authentication for patch updates
C. Provide an MD5 hashfor each file
D. Implement a RADIUS authentication
Correct Answer: C
If we put an MD5 has for each file we can see if the file has been changed or not. MD5 is an algorithm that is used to
verify data integrity through the creation of a 128-bit message digest from data input (which may be a message of any
length) that is claimed to be as unique to that specific data as a fingerprint is to the specific individual.
QUESTION 32
MIMO technology in the 802.11n standard provides for which of the following benefits?
A. Channel expansion
B. Gigabit wireless bandwidth
C. Multipath support
D. Channel bonding
Correct Answer: C
QUESTION 33
A technician is installing a PoE switch for VoIP phones. Which of the following is the technician MOST likely going to
configure on the switch?
A. NAT
B. QoS
C. PAT
D. DHCP
Correct Answer: B
QUESTION 34
Which of the following is a document that is used in cyber forensics that lists everywhere evidence has been?
A. Warrant
B. Legal document
C. Chain of custody
D. Forensic report
E. Documentation of the scene
Correct Answer: C
QUESTION 35
Which of the following Ethernet features will allow increased FCoE network throughput as long as all network devices
recognize its specific size?
A. Frame relay
B. TCP offloading
C. Jumbo frame
D. Quality of service
E. Equal cost multipath
Correct Answer: C
QUESTION 36
A company only wants preapproved laptops to be able to connect to a wireless access point.
Which of the following should be configured?
A. SSID disable
B. ACL rules
C. WPA encryption
D. MAC filtering
Correct Answer: D
QUESTION 37
A network technician must utilize multimode fiber to uplink a new networking device. Which of the following Ethernet
standards could the technician utilize? (Select TWO).
A. 1000Base-LR
B. 1000Base-SR
C. 1000Base-T
D. 10GBase-LR
E. 10GBase-SR
F. 10GBase-T
Correct Answer: BE
1000BASE-SX is a fiber optic Gigabit Ethernet standard for operation over multi-mode fiberwith a distance capability
between 220 meters and 550 meters. 10Gbase-SRis a 10 Gigabit Ethernet LAN standard for operation over multi-mode
fiber optic cable and short wavelength signaling.
QUESTION 38
OFDM, QAM and QPSK are all examples of which of the following wireless technologies?
A. Frequency
B. Modulation
C. RF interference
D. Spectrum
Correct Answer: B
QUESTION 39
A technician needs to install software onto company laptops to protect local running services, from external threats.
Which of the following should the technician install and configure on the laptops if the threat is network based?
A. A cloud-based antivirus system with a heuristic and signature based engine
B. A network based firewall which blocks all inbound communication
C. A host-based firewall which allows all outbound communication
D. A HIDS to inspect both inbound and outbound network communication
Correct Answer: C
A host-based firewall is a computer running firewall software that can protect the computer itself. For example, it can
prevent incoming connections to the computer and allow outbound communication only.
QUESTION 40
Which of the following network topologies describes a network where each node is connected to multiple devices?
A. Mesh
B. Bus
C. Star
D. Ring
Correct Answer: A
We offer more ways to make it easier for everyone to learn, and YouTube is the best tool in the video. Follow channels: https://www.youtube.com/channel/UCXg-xz6fddo6wo1Or9eHdIQ/videos get more useful exam content.
Latest CompTIA Network+ N10-006 YouTube videos:
Share 40 of the latest CompTIA Network+ N10-006 exam questions and answers for free to help you improve your skills and experience ! Easily select the complete N10-006 Dumps:https://www.leads4pass.com/n10-006.html (1703 Q&A) through the exam! Guaranteed to be true and effective! Easily pass the exam!
[PDF] Free CompTIA Network+ N10-006 pdf dumps download from Google Drive: https://drive.google.com/open?id=1oME3_Ww4GaPrmj9dRokJJL9iC6d4agEQ
[PDF] Free Full CompTIA pdf dumps download from Google Drive: https://drive.google.com/open?id=1cFeWWpiWzsSWZqeuRVlu9NtAcFT4WsiG
Lead4pass Promo Code 12% Off
related: https://www.passontheinfo.com/helpful-latest-citrix-cca-n-1y0-253-dumps/
related Network+: https://www.dumpsdemo.com/?s=network